Security Information and Event Management
SGBox Next Generation SIEM and SOAR - All in One
SGBox Security information and Event Management (SIEM) Platform allows the centralized collection of all information from multiple devices and security systems, to gain real-time insight into potential threats and respond quickly and effectively to incidents.
SGBox Next Generation SIEM and SOAR
SGBox’s SIEM offers advanced centralized data collection and security data processing capabilities. It is a Next Generation technology that combines traditional SIEM capabilities with SOAR (Security Orchestration Automation and Response), UBA (User Behavior Analytics), Threat Intelligence, and Network Vulnerability Scanner technologies.
A key factor is the ability to set correlation rules that, thanks to machine learning processes, automatically activate in the event of an anomaly or a specific type of attack. This translates into the ability to respond quickly and precisely to attacks, incidents, or malfunctions through a Detection activity that anticipates the occurrence of attacks and determines the most effective way to intervene. The analysis and reporting of security events are also preparatory for the Security Operation Center (SOC) team
With SGBox, you can create an aggregate display with all the information gathered from log collection, vulnerability scan, and endpoint status. The collected information feeds a correlation engine and analytics system to provide a full network security posture and adopt automatic responses against cyber security threats.
Bulwark Technologies is an authorised distributor for SGBox SIEM And SOAR Platform
SGBox SIEM in Action
SGBox helps your organization track user activity, monitor compliance violations, and generate reports for audit purposes, providing organizations with valuable information about their security posture, anomalies, and risk scenarios.
Reduce Risks in a Simple and Effective Way.
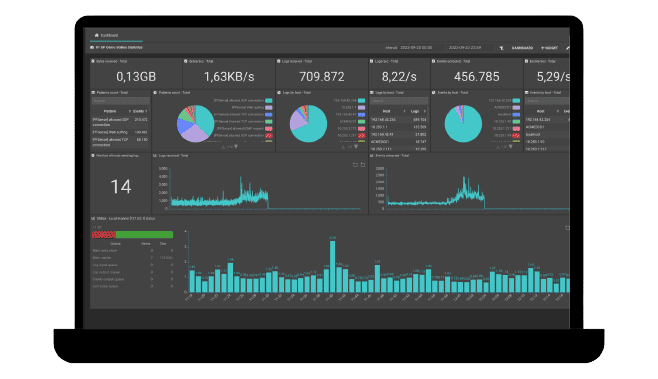
Improve Security Activities with SGBox SIEM Platform
Detection of Threats
SIEM allows you to quickly detect security events, reducing response time and mitigating any damage caused by cyber attacks or abnormal behavior.
Pro-Active Monitoring
With its ability to analyze and correlate data from multiple sources, SGBox’s SIEM allows you to identify suspicious activity or unusual behavior, allowing you to take action before security incidents occur.
Compliance
SIEM helps companies meet regulatory compliance requirements, such as GDPR, ISO 27001 or PCI DSS, by providing detailed reporting and data storage for audit purposes.
Operational Efficiency
Centralization of data and automated reporting simplify security monitoring and reduce the workload of system administrators.
How does SGBox SIEM Works?
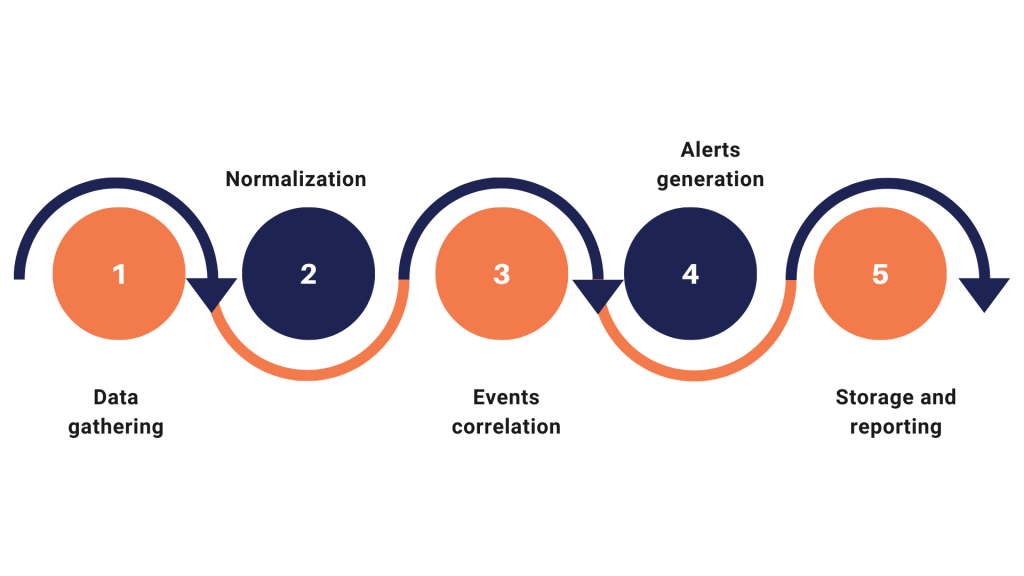
SIEM collects security data from different sources, such as firewalls, intrusion detection systems, sntivirus, and many more.
Data is standardized and normalized in a common format to facilitate analysis
The data is analyzed to identify the correlations between the events, in order to identify any abnormal patterns or behaviours.
If suspicious or potentially harmful events are detected, the SIEM generates alerts that are sent to security administrators for analysis and intervention
Data is stored for compliance and reporting purpose, enabling long-term analysis and reporting for audits and inspections
The elements of SGBox SIEM
Security Information and Event Management (SIEM) has evolved and incorporated new capabilities that provide added value to the threat detection and mitigation process. This evolution of capabilities and features is referred to as “next-gen SIEM.” Implementing a next-generation SIEM solution provides advanced methods to secure data and consolidate IT infrastructure defense processes.
Log Management
Collection of data and information from any computer system.
Threat Intelligence Feed
Proactively detect the most complex threats before they occur.
User Behaviour Analytics
Analysis of user behavior through advanced monitoring systems.
Network Vulnerability Scanner
Identify vulnerabilities and analyze the security status of your IT infrastructure.
Log Management
More Than a Log Repository
SGBox can collect a large amount of events from numerous computer security solutions (NIDS, firewalls, AV, network devices, etc.), web application attacks, and Breach data attempts that can be displayed in a dynamic dashboard to facilitate surveys.
- The Log Management module can manage logs of events related to the security of any device
- the Log Management module automatically collects and classifies information to provide a clear overview of each organization’s security
- The log is stored, encrypted and signed to ensure data integrity and comply with the main regulations
Uncommon Simplicity
Powerfully designed and intuitive log aggregation, tagging, filtering, and searching for effective troubleshooting. Drill-down events, starting from an overview of historical data by entering in detail to analyze the single event.
Data Integrity
Strong encryption with asymmetric keys are used to grant efficient log encryption of stored data. Timestamp and sign are used to certify the integrity of data. Unlimited data volume can be stored without time limitations.
Unlimited Log Format
SGBox is able to collect any kind of log data format. In case of unknown log formats, such as custom application, is simple to generate the appropriate patterns to recognize all the security events.
Threat intelligence Feed
Proactive defense against complex threats
Threat intelligence feeds are continuous streams of actionable information on existing or potential threats. SGBox collects security data on IoCs such as anomalous activity and malicious domains and IP addresses, from a number of sources. SGBox can then correlate the data and process it to produce threat intelligence and management reports.
With SGBox SIEM the customers can access a number of open source or commercial threat intelligence feeds and sources. All collected information is aggregated into detailed reports, from which you can get a complete view of the security status of your IT infrastructure.
Early Detection of Threats
By analyzing intelligence feeds, you can detect threats early and counter them before they happen.
Reduction of Time of Remediation
Proactive intervention significantly reduces response time to attack and limits potential damage to your IT infrastructure..
Protection Over Complex Threats
Through intelligence feeds it is possible to analyze information and data from different internal and external sources, to identify methods, motivations and techniques used by attackers.
User Behaviour Analytics (UBA)
Tracks and collect information about user behavior using advanced monitoring systems. SGBox UBA provides historical data analysis to detect potential suspicious activity that deviates from normal user behavior. Any activity that deviates from this baseline gets flagged as an anomaly. The UBA can identify user accounts taken over by attackers, because they exhibit anomalous behavior compared to the real business user.
SGBox UBA can monitor accounts with administrative or escalated privileges, to ensure they are not being misused which includes policy violations or neglectful acts.
Accelerate Threat Unting
Rapidly identify anomalous entities without human analysis. Receive notification when there is an unusual volume of events.
User Related Risk
User behavior can be associated to a risk categories not only on its volume. A set of dedicated widgets show, through trend indicators, the risk associated to users.
Quick Implementation
Quickness and ease of use. No advanced configuration needed because the SGBox UBA automatically checks for all different situations starting from events.
Network Vulnerability Scanner
Vulnerability Management and Advanced Reporting System
With vulnerability scanning module – understand the cyber exposure of all assets, including vulnerabilities, misconfigurations and other security health indicators. Schedule custom vulnerability scan policies to every asset or group, Users receive automatic reports and alerts. remote scanning sensors, monitor the vulnerability status of remote or branch offices.
With CVSS (Common Vulnerability Scoring System) rate the scan results for every asset or group. Advances reporting system offers a huge number of reports out-of-the-box, increasing the level of details based of the different recipients.
Vulnerability Prioritization
Prioritize remediation based on asset criticality, threat context and vulnerability severity. Prioritize which exposures to fix first, if at all, and apply the appropriate remediation technique.
Compliance
Support compliance requirements of major regulations such as GDPR, SAMA Cyber Security Framework, PCIDSS and ISO27001.
Automate Processes
Live discovery of any digital asset across any computing environment. Leverage different pre-built report template, automate scans and share data with your IT systems
Incident Management
Management of security incidents
The Incident Management module provides an integrated platform to manage the incidents and anomalies detected from the other SGBox modules.
SGBox Incident Management is the key to reducing time, complexity and costs related with managing IT incidents.
The automatic alarm correlation system can highlight potential malicious activity, aggregating the alarms generated by different correlation rules to provide a more detailed overview of what is happening within your IT infrastructure.
Ticketing for technical assistance
Manage detected security tickets, assign them to a specific member of the investigation/resolution team, follow the ticket history to its complete resolution and display multiple statistics to improve the response to anomalies.
Graphical View of Incident detail
This visualization allows to graphically represent the structure of the incident, highlighting the dependencies between the components of the alarms and other events that can indirectly contribute to the accident. Get detailed information about which users, IP addresses or hosts are related to a given problem
SGbox Case Management
Dynamic case management provides direct interaction with all incident-related data and actions, allowing analysts to respond more quickly and flexibly. SGBox’s case management capability is fully integrated with workflow and Playbooks to consolidate the entire incident response process.
Advanced Event Search
Deeper visibility on connected devices
Detect, Verify and Resolve Network Performance Issues through the Advanced Event Search module. SGBox provides real-time devices health monitoring and offers detailed insights into various problematic areas of the network.
The monitoring capability has been designed to complete the SGBox SIEM & SOAR platform preventing devices fail and allowing the support team to drill down to the root cause of the issues.
Personalized Dashboard and Widgets
The real-time performance graphs can be configured as dashboard widgets to let you see live performance trends as soon as they login.
Open Monitoring System
Monitor all the systems and devices in your IT infrastructure. You can deploy multiple monitoring probes maintaining centralized management.
Ready and Easy to Use
SGBox is a powerful and easy-to-use solution, which is suitable for businesses of all sizes. All main protocols are supported, there is no need for additional plugins or downloads.
Active Directory Auditor
Full visibility on Windows systems
Constantly monitor the status of Active Directories, determine risk, and warn when set KPI thresholds are exceeded. This module is seamlessly integrated with all other SGBox features, and is capable of generating lists that can be used by other modules to perform specific tasks such as event correlation and filtered reports.
SGBox includes Windows auditing capabilities, to help organizations remain compliant with data protection requirements, identify potential threats early, and help to reduce the risk of a data breach.
Advanced Control
SGBox includes advanced control capabilities on MS Active Directory systems to help businesses meet data protection requirements.
Full Visibility
Active Directory Auditor provides a clear picture of all changes to AD resources, including AD objects and their attributes.
Immediate Response
It helps detect and respond to internal threats, misuse of privileges, and other Compromise Indicators (ioc).
File Integrity
The crucial role of the SGBox SIEM
File integrity monitoring allows you to detect unwanted changes in your business data in real time and quickly alert your security team in case of anomalies. SGBox not only provides broad visibility into file server activities and connected storage devices, but also provides advanced tools to monitor file integrity and protect against internal and external threats.
When detecting unauthorized activity or threats, SGBox issues immediate alerts and allows you to take proactive measures to protect file integrity, such as blocking responsible users.
Detailed Monitoring
SGBox accurately records who accesses files, what changes are made, who reads or deletes files, allowing complete monitoring of file activities.
Anomalies Detection
SGBox’s advanced features can automatically detect abnormal behavior, such as unauthorized changes or massive file deletions, and report potential threats in a timely manner.
Events Correlations
SGBox correlates information from various sources, allowing you to detect suspicious activity and threats through data analysis.
Event Correlation and Response System
Alerts and Automated Response. Reduce the reaction time to a threat by sending a warning message
Define rules and detect threat scenarios. SGBox aggregates and analyzes log data from across your network applications, systems and devices, making it possible to discover security threats alerts or trigger automatic countermeasures using scripts or interacting with external systems via API’s.
SGBox easy and intuitive GUI allows the creation of complex chained event based correlation rules in a few simple steps. The correlation rules may be used on real time or historical data.
Predefined Rules Set
It is possible to choose correlation rules from many predefined templates, constantly updated and guaranteed by the experience of our Security Engineers.
File Integrity Monitoring
Monitor file activities to protect sensitive information from theft, loss and malware. Check and view details or changes made to files and folders identifying an attack.
Automated Response
SGBox can engage automated response in case of threats by launching scripts or interacting with security components via API or APPs to mitigate theats.
Easy Licensing Model
The first SIEM at a predicable price, unlimited data and transparent licensing model.
The license cost is based on the total number of devices sending logs, not on the obsolete volume of data or event per second (EPS) count.
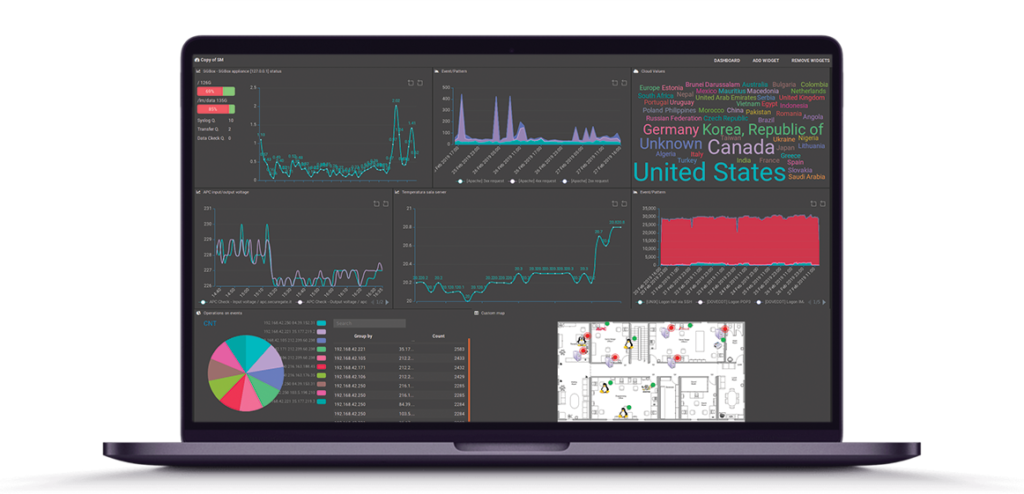
SIEM for the Compliance
Automate process to achieve compliance by responding to a lot of controls required in the auditing phase like: GDPR, PCIDSS, SOX, ISO 27001 and SAMA Cyber Security Framework.
Cloud SIEM - reduce costs and management efforts with Cloud
SGBox’s Cloud SIEM takes advantage of the full potential of Security Information and Event Management (SIEM), with the flexibility and ease of use of the Cloud in saas mode (Software as a Service).
Cloud SIEM eliminates management costs by storing data hosted in the SGBox Cloud, unlike an on-premise system that keeps data within organizations and requires additional hardware to be installed.

Team of Experts
The knowledge of our experts allows you to develop an IT security project quickly, eliminating the need to train internal staff.
No Hardware Needed
The cloud-based system eliminates the need for physical infrastructure such as storage and servers dedicated to the SIEM, thus facilitating deployment.
Continuous Monitoring
SGBox Cloud infrastructure and services are always monitored by our expert team. All issues will always be under control.

Download Corporate Brochure
SGBox Next-Gen SIEM & SOAR
SGBox is a highly flexible and scalable solution for IT security. Choose the modules which your company needs and implement it without any modification to your network infrastructure.
Product Demo
SGBox Next Generation SIEM in Action with Bulwark Technologies
Schedule a Demo with Bulwark Technologies and explore the full capabilities of SGBox SIEM and SOAR Platform.
Schedule a FREE Demo
"*" indicates required fields
