Third Party and Vendor Risk Management Solution
Vendor Risk Management Solution from RiskXchange enables organizations to effectively manage, monitor performance and mitigate risk across supplier networks.
Vendor Risk Management Solution from RiskXchange
A single disruption or unmitigated cybersecurity vulnerability anywhere along the supplier network can quickly turn into a much larger issue, impacting share price, bottom-line profits and brand value. Discover, assess, continuously monitor and reduce vendor and third party risks.
RiskXchange Platform provides a 360-degree vendor risk management solution with integrated security compliance & governance assessments and instant security ratings to promote risk-based decisions, when it comes to your third parties. RiskXchange Vendor Risk Management solution helps streamline the global supplier cyber risk and compliance management processes with actionable insights that enhance business value.
Bulwark Technologies is an authorised distributor for RiskXchange Third Party and Vendor Risk Management solution.
Enforce Third-party Security with our Solutions:
Security Risk Ratings
RiskXchange Security Risk Rating represents an aggregate measure of security risk across your entire digital ecosystem. Deliver real-time continuous risk ratings and analysis using our advanced risk quantification methods. Identify, locate, and mitigate risks immediately.
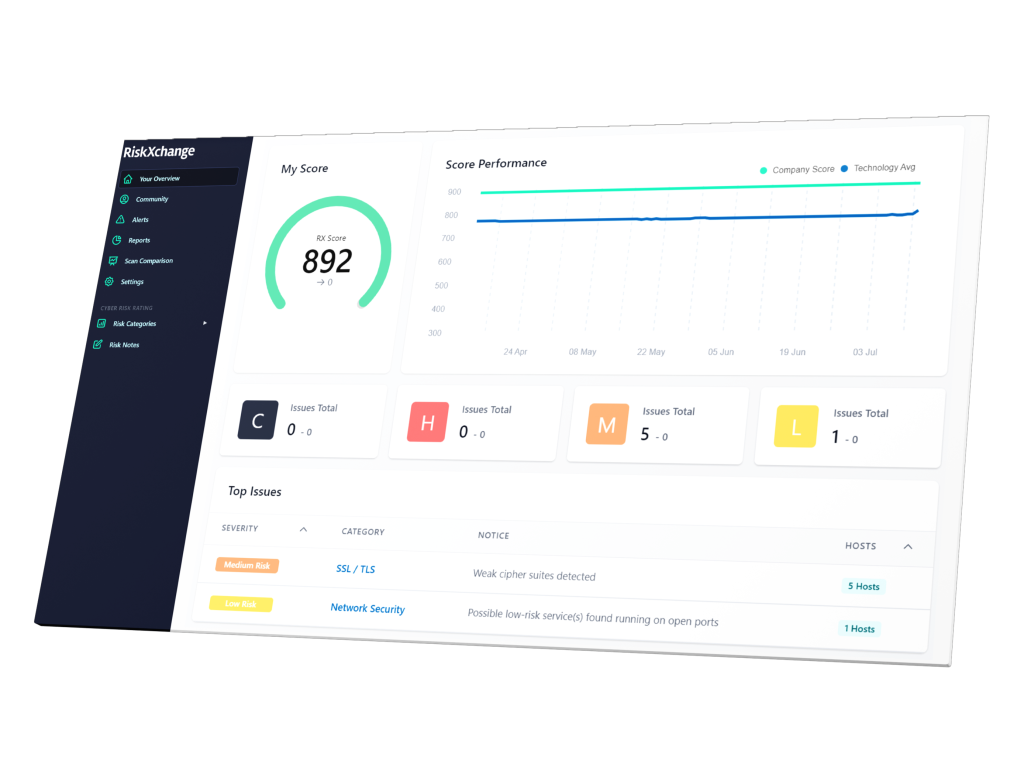
Security Risk Ratings Key Features
Continuous Visibility
Instantly get a security rating to understand and monitor the security posture of any organisation across the globe. The RiskXchange platform non-intrusively collects data from the internet for an objective, outside-in perspective.
Realtime Risk Insights
Instantly understand your risk insights profile and that of your suppliers and drill down into individual risks shared across your infrastructure as well as groups of the suppliers within your supply chain
Focused View Of Risk
Identify the most critical areas of risk for your organisation. Security Ratings offer business-level reporting across a range of risk factors, including application and network security, encryption, DNS security, email security, malware risk, data breaches and much more.
Real Time Alerts
RiskXchange comes with a range of default notifications across groups and companies and allows you to create and manage custom real-time notifications. These can be used for in-app, email alerts, or Microsoft team triggers.
Risk Notes
Accept specific risks identified by the RiskXchange platform with a detailed context of discovered threats.
Breach Notification
Discover Data Breaches within your third parties, know what data has been exposed and receive real-time notifications.
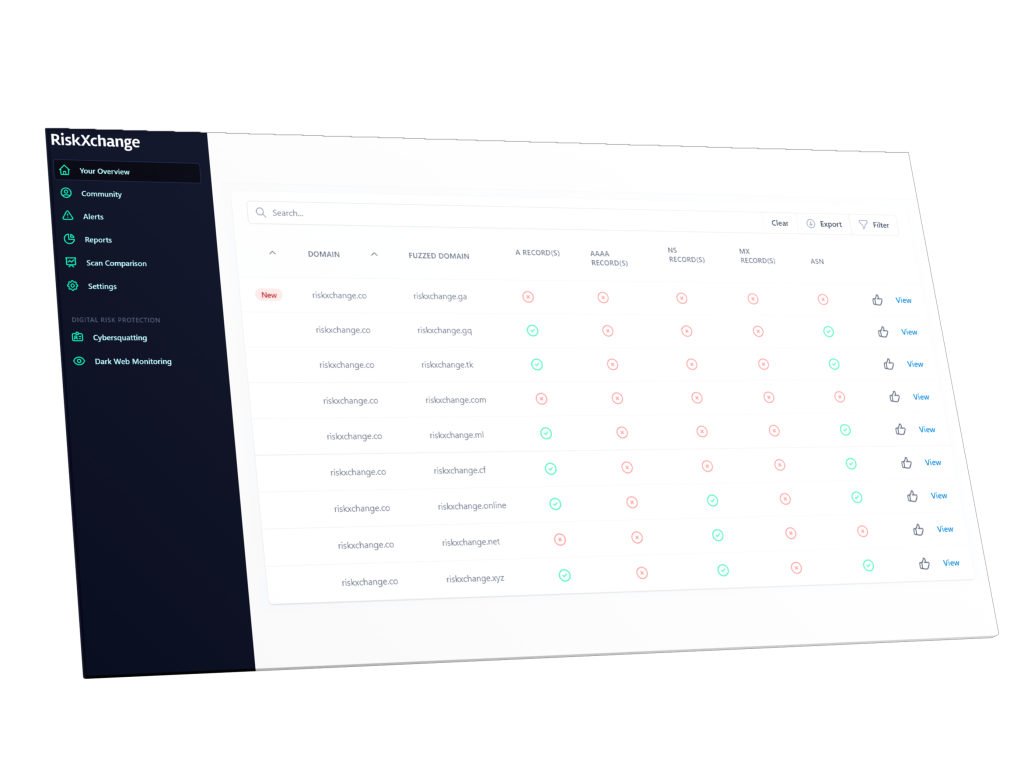
Digital Risk Protection
Your data can be found everywhere, from your network to your digital supply chain to outside sources like Dark Web sites. Having this data leaked, stolen, or given to competitors could have a significant impact on your business. Protect your brand and business with the RiskXchange fully-integrated Digital Risk Protection feature.
Digital Risk Protection Key Features
Account Takeover Prevention
Attackers use leaked credentials data to take over employees’ accounts with privileged access, including accounts of board members, senior executives, developers, and systems administrators.
RiskXchange Account Takeover Prevention system can detect and alert these corporate credential exposures to stop attackers from using leaked credentials to gain entry into the company’s accounts and systems.
Impersonation Protection
Fraudsters use typosquatting to impersonate companies’ brands to target and defraud their users and customers to harvest credentials or spread disinformation.
RiskXchange Impersonation Protection system continuously monitors your domains and alerts you when your brand is being impersonated, allowing you to investigate and launch takedowns to prevent reputational damage or loss of company information.
Dark Web Monitoring
RiskXchange prevents your company from a data breach online by continuously monitoring a wide range of open, deep, and dark web sources, including closed sources, used by attackers that target organisations.
RiskXchange Dark Web Monitoring system delivers accurate, actionable, configurable alerts that will empower your security team to stop attacks by identifying threats before they impact your business.
Attack Surface Management
Reduce your organisation’s cyber risk by monitoring, tracking and mitigating risk across your attack surface around the clock.
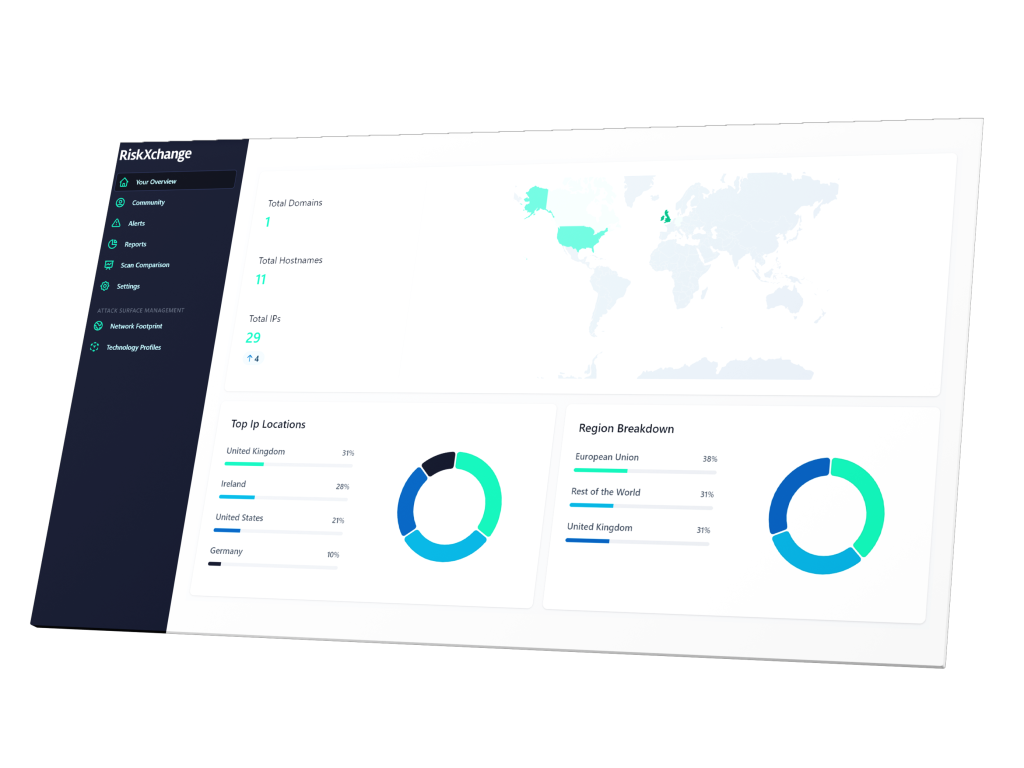
Attack Surface Management Key Features
Continuous Attack Surface Management
Continuous 24/7 assessment of your attack surface in real time.
Asset Inventory
We accurately identify your internet assets across your attack surface and that of your third-party supply chain.
Real Time Alerts
The platform has a real-time alert system that will alert you about new cyberattacks.
Complete Visibility
Complete visibility into everything you own, including IP addresses, domains, certificates and cloud assets.
Security Automation
Create alerts for new anomalies and automate key cybersecurity risk management functions.
Track Your Digital Footprint
Monitor all activities taking place in your infrastructure, including your vendor's.
Extensive Data Sources
We refresh your data every 24 hours from DNS Records, Netblocks, Domain registrars, Honeypots, Business registration databases and other sources
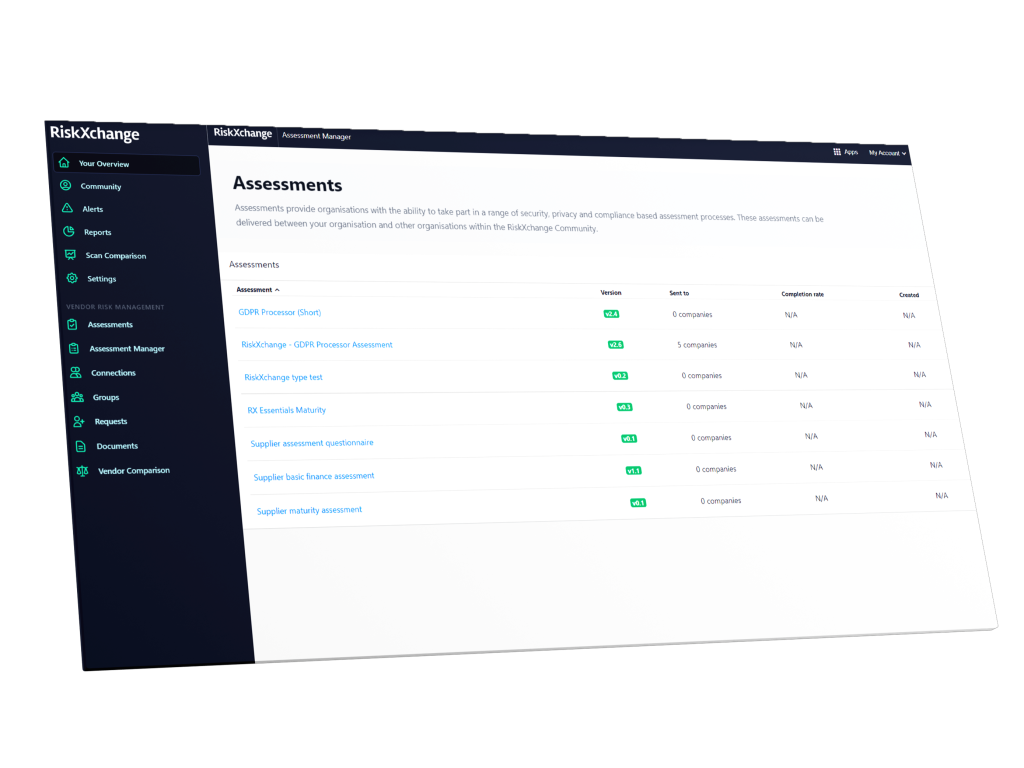
Security Assessments
RiskXchange provides visibility into the internal security posture of your third-party suppliers, plus how well they adhere to required compliance initiatives. This ‘inside-out’ view of a company relates to critical controls that cannot be discovered by external scanning analysis
Vendor Security Assessment Key Features
All in One Place
Upload, create, and modify as many assessments as required for your third-party suppliers.
Prebuilt Assessment
Use the RiskXchange Cyber Essentials predefined assessment to get a handle on key control points.
Easy to Use Results
Presentation of the assessment results in a consistent and easy-to-review manner
Automated Process
Automated assessment distribution and chasing for completion.
Consistent Scores
Automatic and consistent scoring across third-party assessments.
Compliance Check
Ability to look across all assessments for non-compliancy and upload supporting evidence documentation.
Vendor Risk Management Key Capabilities:
A Proven TPRM Maturity Process
Speed time to value and mature your TPRM program with our expert planning and advisory services. We’ll help you prioritise your vendors and suppliers, define assessment strategies, and accommodate compliance.
Continuous Risk Monitoring
Validate vendor controls by correlating assessments with monitoring for cyber threats (e.g. website vulnerabilities, leaked credentials on the dark web, etc.) and potential business threats (e.g. brand, financial, operational, regulatory, legal, etc.) for a more complete risk score.
Smart Assessments
Measure vendor and supplier internal controls and procedures and access risk data with a library of 75+ assessments covering everything from IT security controls to corporate social responsibility issues – or build custom assessments to meet specific needs.
Shared Vendor Networks
Scale your TPRM program with shared networks of completed vendor risk assessments. The RiskXchange Exchange enables you to check compliance quickly for any organisation on the exchange
Continuous Third-party Cyber Risk Management

Product Demo
See RiskXchange Vendor Risk Management Solution in Action with Bulwark Technologies
Schedule a demo now with Bulwark Technologies and experience the full capabilities of RiskXchange Vendor risk management solution.
- Security Risk Rating
- Continuous Attack Surface Management
- 360Degree Vendor Risk management
- Digital Risk Protection including Dark Web
- Integrated security assessment
- Real-time alerts and actionable intelligence
Schedule a FREE Demo
"*" indicates required fields
