Votiro
Zero Trust Content Security with Data Detection and Response in One Platform
Votiro make file-borne threats and privacy risks a thing of the past.
Votiro is Zero Trust Content Security with Data Detection and Response in one platform. With proactive file-borne threat prevention, real-time privacy and compliance, and actionable data insights, our Zero Trust solution protects you from countless digital threats that pose unnecessary risks to your organization, your customers, and your reputation
Votiro Zero Trust Content Security solution is trusted by industry leaders around the world to deliver billions of safe files between commercial and government organizations, their employees, and the customers that rely on them. The Votiro Cloud solution is an open-API that detects, disarms, and analyzes content at the speed of business – delivering teams with fully-functional files, reduced risk, lower costs, and increased productivity. Votiro Cloud proactively eliminates fileborne threats targeting email environments, collaboration platforms, data lakes, supply chains, web downloads, B2C digital interactions, and more
Bulwark Technologies is an authorised distributor for Votiro Zero Trust Content Security with Data Detection and Response.
Why Votiro is Perfect for Data Security
Votiro proactively detects known and unknown threats in content attempting to enter your organization, then proactively disarms the file before it ever reaches the endpoint. And we don’t stop there. Personal Identifiable Information (PII) is also handled in real-time to ensure access is restricted to the right people at the right them, while keeping your organization compliant well-ahead of recurring audits.

Privacy & Compliance
Never second-guess an uploaded customer document again. Keep sensitive information private and in the right hands.

Threat Analytics
Keep your entire agency network safe from file-borne threats. Get actionable insights into your files and risk surface.

Content Collaboration
Patient privacy remains top-of-mind with seamless data security. Protection where work happens most – locally and remote.

Web Downloads
Don’t let malware slow-down the supply chain or bring ports to a stop. Prevent hidden threats in files downloaded from the web

File Uploads
Store and facilitate bulk data without worrying about file-borne threats. Stop malware from entering web portals and applications.

Data Storage
Keep the grid running by eliminating the threat of digital threats like malware. Ensure your data lakes are free from hidden threats.

Email Attachments
Work with all stakeholders without slowing down or compromising data. Prevent 100% of file-borne attacks delivered via email.

File Transfers
Protect your endpoints from data risks – no matter where they are.

Web Apps API
Don’t see your industry? We’ll help you find a solution that works for you.
How Votiro Works:
Welcome to the new world of Zero Trust.
Votiro’s patented technology is the first of its kind, ensuring Zero Trust security in every file entering and leaving your systems – without ever interrupting your productivity. Now, you can work efficiently, confidently, and safer than ever.
Step 1
Unknown file is received
Step 2
Dissect file into content, templates, and objects
Step 3
Rebuild the content on top of safe file templates – removing any potentially malicious content.
Step 4
Deliver a 100% safe, usable file
Dashboard Overview - Votiro
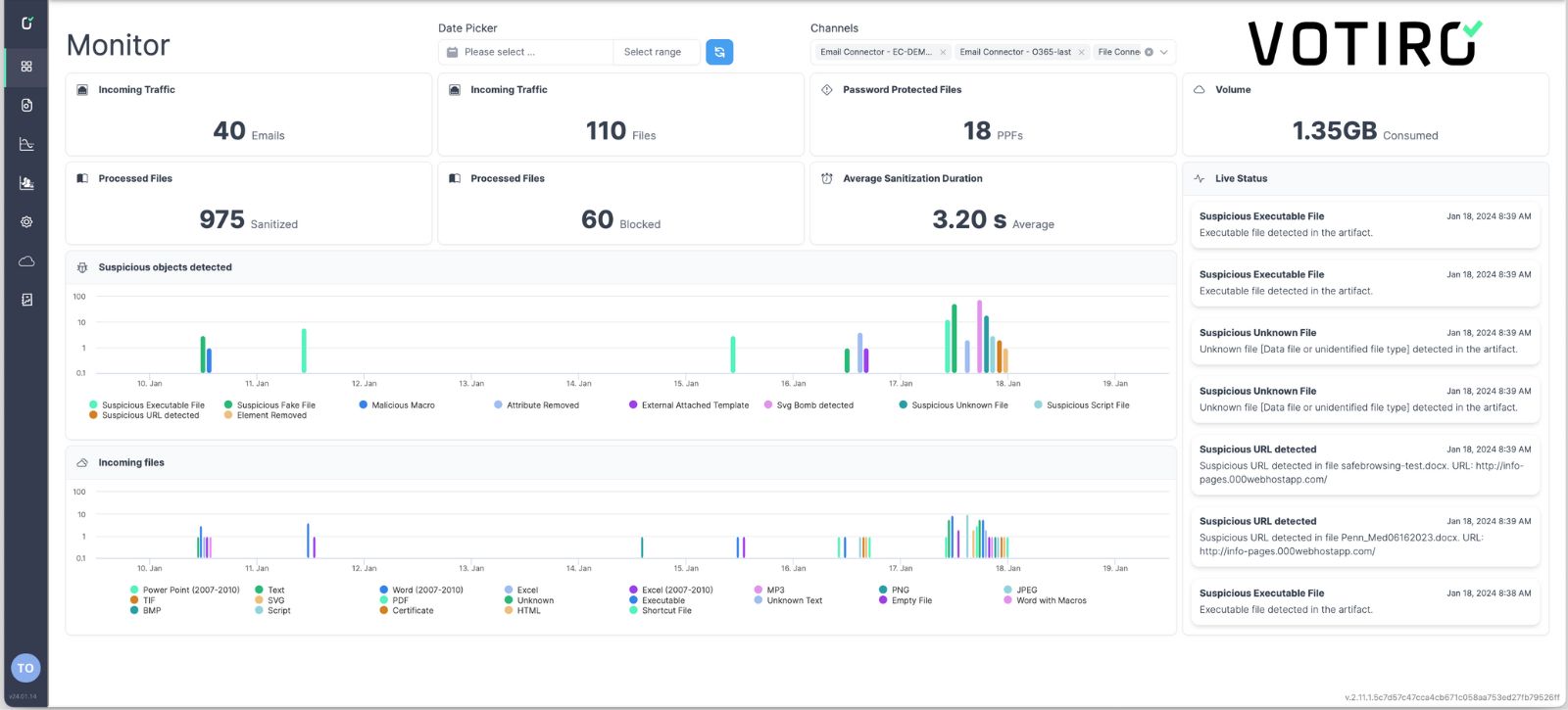
- See all information at a glance from the monitor mode dashboard.
- Customise the data you are seeing by date and channels (email, content. collaboration platform, browser downloads, etc).
- Understand high level trends in suspicious file types, harmful elements being removed, where more suspicious files come from, and more.
- See how many incidents need further review.
- Drill down into individual files or events to investigate potential threats or compliance risk.
- Use customizable filters for quick and effective threat hunting.
- On a per-item basis, see how many files were sanitized or blocked and how many suspicious objects for detected. This will help to understand the zero day attacks that you have prevented.
- Deep dive into the details to learn more about which suspicious elements, URL’s macros, and more were removed from the file before being delivered to your endpoints.
- Take a closer look into your organization including who is most targeted by suspicious file and emails.
- Identify the most suspicious objects that are being removed for instance other employees receiving files with suspicious macros or images?
- See your total win events - these are events in which Votiro’s RetroScan highlights a previously unknown variant of malware that was removed before it got to your endpoint now you can tell management how many zero days were prevented.
- Votiro will tell you which incoming and outgoing file contains sensitive data.
- You can see who sends and receives PII, Phi and PCI - even if they aren't supposed to - in order to update your policies on who is able to access specific content in order to remain complaint.
- At a glance, you can identify which major regulations you’re at risk of becoming non compliant with
- We understand you may not want every single item to be sanitised what keeps you in control of your experience
- Votiro allows for complex flexibility on which policies you’d like to implement.
- Set custom policies for various file types, data types, situations, n channels to fit what's best for your business operations.
- Easily configure policies and controls within the interface to make customization a breeze
Votiro
Votiro pioneered Zero Trust Content Security. Today, we go beyond existing solutions to provide the very best in threat prevention and data security.
Every file is examined and sanitized no matter what.
the rest...
NG Antivirus
Predictions based on a signature-based list or collaborative database, which leaves room for zero day threats to breach your endpoints.
Sandboxing
Virtualization aimed at predicting outbreaks, but can slow down productivity and still allow some malware to sneak through.
EDR/MDR/XDR
Solution that highlights threats that have reached the endpoint and alerts for after-the-fact mitigation – which is far too late for true protection.
Votiro - Zero Trust Content Security
See how Votiro protects your data in real-time
Votiro proactively eliminates fileborne threats targeting email environments, collaboration platforms, data lakes, supply chains, web downloads, B2C digital interactions, and more.
