Securing Your Inside Perimeter
Manage privileges dynamically, convert user activities into actionable insights, and respond swiftly to potential threats. Transform your organization’s human risk into human assets.
Bulwark Technologies is an Authorised Distributor for Syteca in Middle East.
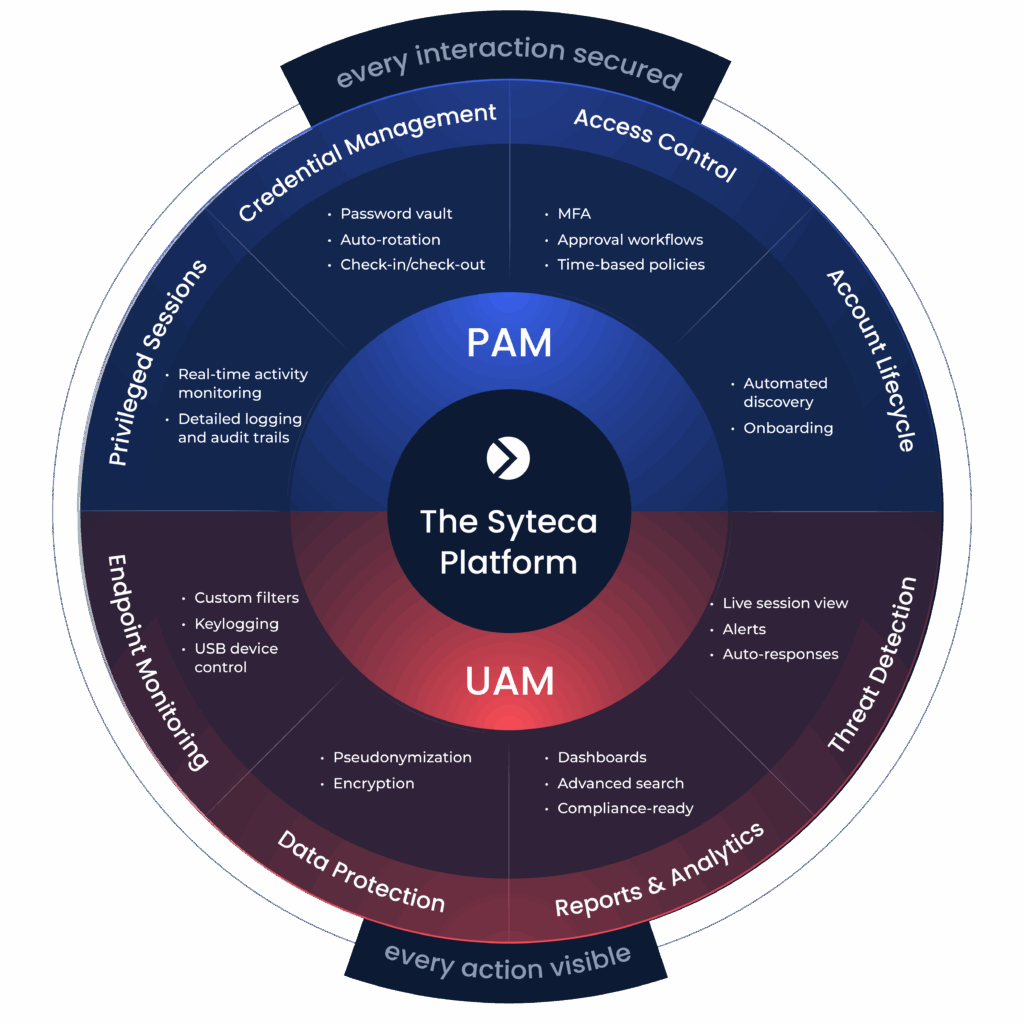
What is Syteca
Syteca is a flexible platform that redefines inside perimeter security by providing enterprise cybersecurity solutions designed to address your organization’s specific needs. With advanced user activity monitoring and robust privileged access management, Syteca turns vulnerabilities into strengths. Boost efficiency, simplify compliance, and elevate your security, all from within.
More than 1,500 organizations all over the world have enhanced their cybersecurity with Syteca. By monitoring user activity, controlling access, and responding to suspicious events, you can ensure a holistic approach to protecting sensitive data from threats caused by insiders in your organization.
© Syteca
Syteca 7.21 is here.
Shaped by feedback. Powered by innovation.
Complete Perimeter Security
Syteca provides full visibility into user activities and enables precise access controls, empowering you to mitigate insider threats and prevent data breaches. Transform internal risks into security strengths and fortify your organization’s cybersecurity posture from within.
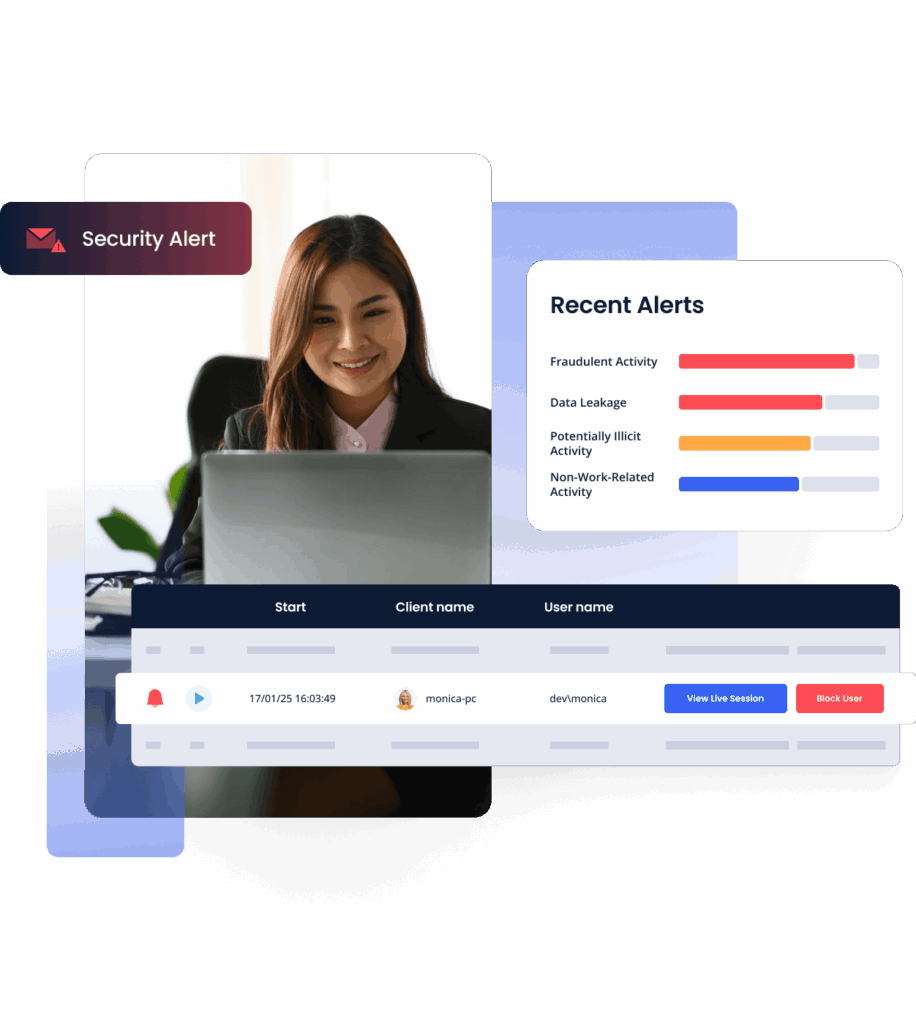
Detect abnormal activity and prevent data breaches
User Activity Monitoring
Stop insider threats before they compromise your security. Effectively prevent security breaches, swiftly detect warning signs, and respond decisively to protect sensitive data and critical systems
Record on-screen activity on endpoints and conveniently review user sessions by filtering and searching through metadata. Export recordings in a secure, tamper-proof format for forensic investigations.
Detect and respond to security threats in real time with a customizable alert system. Watch suspicious sessions live and enable automated responses such as sending warning messages to users, terminating processes, or blocking users.
Generate comprehensive user activity reports ad hoc or on a schedule and export them in various formats for analysis and investigation. With 30+ types of reports, you can get insights into the specific user activity details you need.
Record and search through clipboard operations, keystrokes, and user inputs while preserving user privacy with data pseudonymization. Leverage filtering options and keyword-triggered monitoring to log only what’s most critical for you
Employee activity monitoring software that tracks any user action

Corporate servers
Secure your organization’s critical assets and prevent insider threats’ undesirable financial and reputational consequences.
Physical & virtual Desktop
Improve visibility and control over the organization’s data. Prevent and detect incidents caused by insiders in virtual and physical environments.
Remote Laptops
Monitor the activity of any user inside and outside your protected perimeter to ensure maximum security and transparency.
Jump Servers
Install just one Syteca Terminal Server Client on a jump server to monitor all sessions that come through it.
Record and Monitor Everything
Productivity
Online searches
Network connections
Social media
Upload & download files
Launched Applications
Sent & received Emails
Typed Keystrokes
Visited websites
Connected USB devices
Accessed files/ systems
Screenshots
Improve security and enhance control over privileges
Privileged Access Management
Syteca PAM enables you to manage privileged access across numerous platforms, servers, and endpoints effortlessly. Syteca’s thorough privileged user activity controls help reduce the risk of intentional or accidental privilege misuse. Secure access to sensitive organizational assets, protect privileged account credentials, and monitor user activity — all with a single platform.
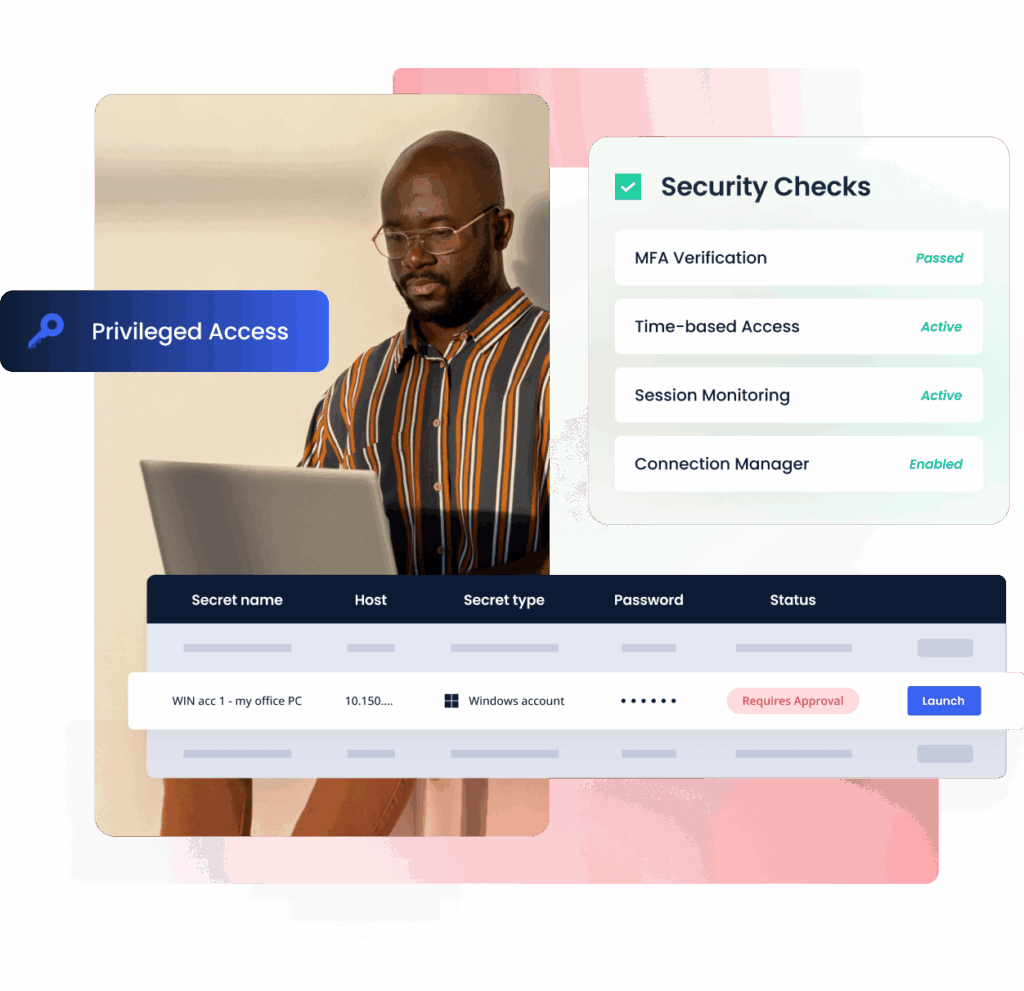
Selectively provide privileged access to users, restrict access by time, set one-time passwords, and manually approve access to critical endpoints. Identify users through multi-factor authentication and secondary authentication (for shared accounts).
Configure customizable rules and schedules to scan and detect all privileged accounts across your domains automatically. Streamline management with instant notifications of newly discovered accounts and bulk onboarding.
Centralize and protect passwords with a secure vault, automated rotation, and role-based access. Enable controlled sharing and checkout of credentials while maintaining detailed access logs.
Establish oversight of privileged user activity by automatically capturing sessions involving the use of secrets and interactions with sensitive or high-risk assets. Log all session-related metadata to create a detailed audit trail for thorough privileged activity reviews.
Product Demo
Unlock the power of Syteca tailored to your needs with Bulwark Technologies
Schedule a FREE Demo with Bulwark Technologies and explore the full potential of Syteca.
Schedule a FREE Demo
"*" indicates required fields
