invicti
Web Application Security with Zero Noise
Build security automation into every step of your SDLC – so your teams can eliminate hundreds of hours of manual tasks each month.
Discover and Crawl
Scan every corner of every app
Detect
More coverage means less risk
Resolve
Fix vulnerabilities with less manual effort
Integrate
Build security into development Seamlessly
Continuously Secure
Stay secure. 24 hours a day. 365 days a year
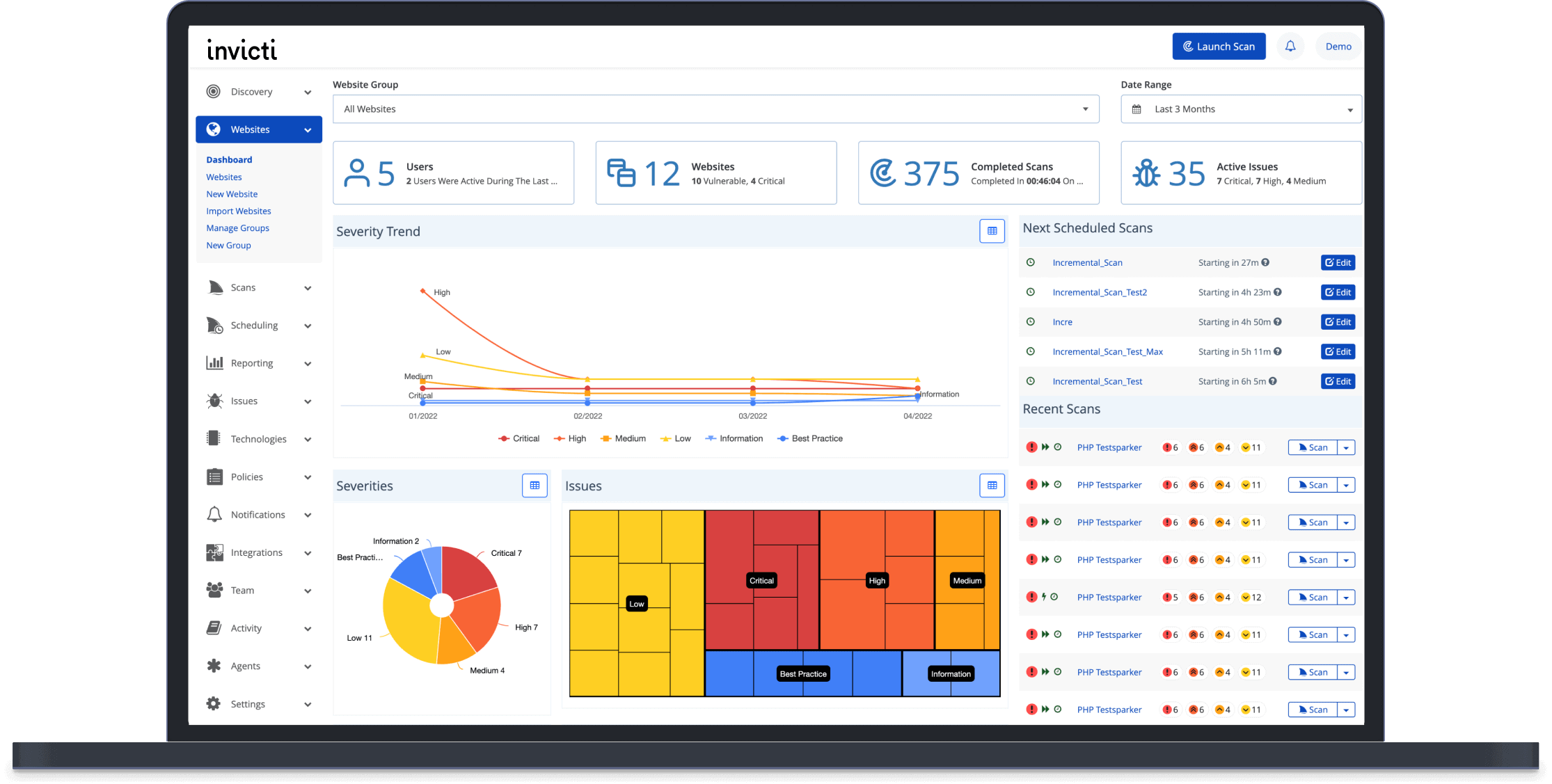
Invicti Enterprise AppSec in 5 Minutes
Cover your Web Application Security Testing with DAST (and more)
DISCOVER + CRAWL
Scan every corner of every app
You can’t secure a web asset if you don’t know it exists. When you have thousands of web assets, your organization is bound to lose track of some of them. This leaves them vulnerable to attacks.
- Gain complete visibility into all your applications — even those that are lost, forgotten, or hidden.
- Scan any type of web application, web service and web API — including first and third-party (open source) code — regardless of the technology, framework or language they’re built with
- Scan the corners of your web assets that other tools miss, with advanced crawling and our combined interactive + dynamic (IAST + DAST) scanning approach.
Continuous Web Asset Discovery
Automatically keep a complete, updated inventory of all your websites, applications, and APIs
Advanced Website Crawling Technologies
Scan script-heavy sites and other web applications most scanners can’t
Easy-to-Configure Authentication
Crawl and scan the password and MFA-protected areas where other scanners fail
Flexible Deployment Options
Choose your ideal deployment model for each environment – from fully on-premise to cloud, and everything in between
Comprehensive Scanning:
Scan every corner of every application with combined IAST + DAST
DETECT
More coverage means less risk
Other application security testing solutions rely on a single type of scanning, such as dynamic (DAST) or interactive (IAST). On their own, each type can miss high-risk vulnerabilities. Invicti’s unique DAST + IAST scanning approach helps you find the vulnerabilities that other tools can’t.
- Detect more vulnerabilities with combined DAST + IAST scanning — developed by the team that pioneered the world’s first IAST.
- Separate the vulnerabilities that truly put you at risk from the ones that don’t.
- Get fast, accurate results with combined signature-based and behavior-based scanning
Industry-Leading Accuracy
Independent benchmarks show Invicti finds more vulnerabilities with fewer false positives than leading scanners
DAST + IAST + API Security Testing
Find the vulnerabilities other scanners can’t detect with our unique approach, combining DAST with IAST and API Security testing
Software Composition Analysis:
Keep using your open-source components without sacrificing security.
Out-of-Band Detection
Find the hard-to-detect OOB vulnerabilities other tools fail to catch
Advanced Manual Scanning Tools
Get the tools you need for manual scanning when automated scans aren’t possible
Technology Version Tracking
Automatically discover all technologies, frameworks, and libraries you’re using – and get notified when they’re out of date
RESOLVE
Fix vulnerabilities with less manual effort
Shrink your security backlog with automation and workflow features that make it easier to manage and assign security tasks. And save your security team hours of manual work every week
- Reduce time-wasting false positives with Proof-Based Scanning™ that eliminates the need for manual verification.
- Automatically create and assign confirmed vulnerabilities to developers.
- Help developers fix issues fast with detailed documentation that pinpoints the exact locations of your vulnerabilities.
Proof-Based Scanning
Eliminate time-wasting false positives
Detailed Scan Results
Give developers all the information they need to resolve each issue on their own
Locate Vulnerabilities
Pinpoint the exact locations of vulnerabilities so developers don’t have to hunt for them
Vulnerability Trend Matrix
See each application’s vulnerability history to track your remediation progress
Dashboards, Reporting, and Compliance
Get the right report for every stakeholder
INTEGRATE
Integrate Invicti with the tools your developers use every day.
- Automatically give developers rapid feedback that trains them to write more secure code — so they create fewer vulnerabilities over time.
- Catch vulnerabilities early in the SDLC so you can save the time, money and headache of post-release security issues.
- Eliminate bottlenecks and reduce the tension between development and security teams by helping developers tackle security tasks on their own.
CONTINUOUSLY SECURE
Stay vigilant with continuous scans and other features that Keep your web applications secure. 24 hours a day. 365 days a year
- Prevent delays and ensure fewer risks are introduced with ongoing scanning and security checks throughout your SDLC.
- Get automatic notifications when a deployed technology becomes outdated — without running a new scan — so your apps stay secure.
- Keep your risk to a minimum — even in an Agile or rapid deployment environment.
Download Corporate Brochure
Invicti - Web Application Security
Product Demo
See how Invicti makes it easier to secure thousands of web assets with Bulwark Technologies
Invicti is a web vulnerability management solution that focuses on scalability, automation, and integration. Based on a leading-edge web vulnerability scanner, the Invicti platform uses proprietary Proof-Based Scanning technology to identify and confirm vulnerabilities, confidently indicating results that are definitely not false positives. Invicti is highly effective both integrated within the SDLC and as a standalone solution
Schedule a FREE Demo
"*" indicates required fields


