HolmSecurity
cybersecurity companies in uae
Next-Gen Vulnerability Management Platform
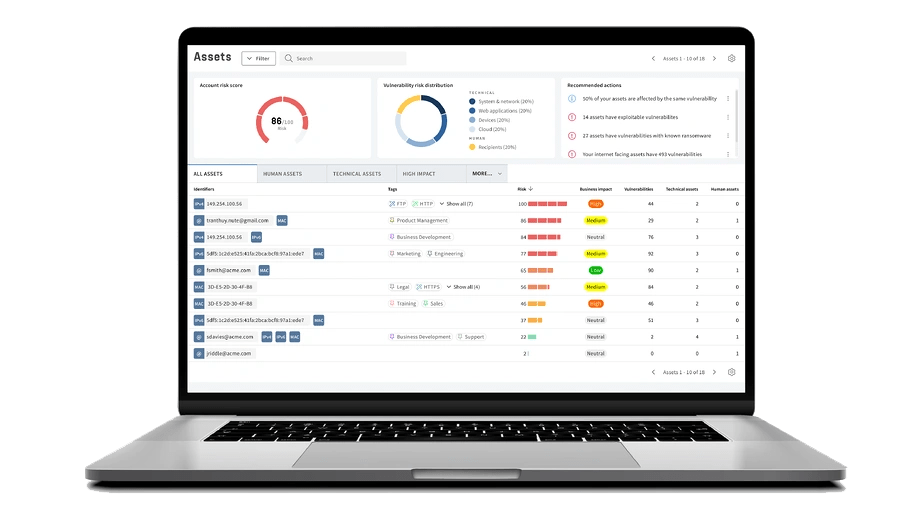
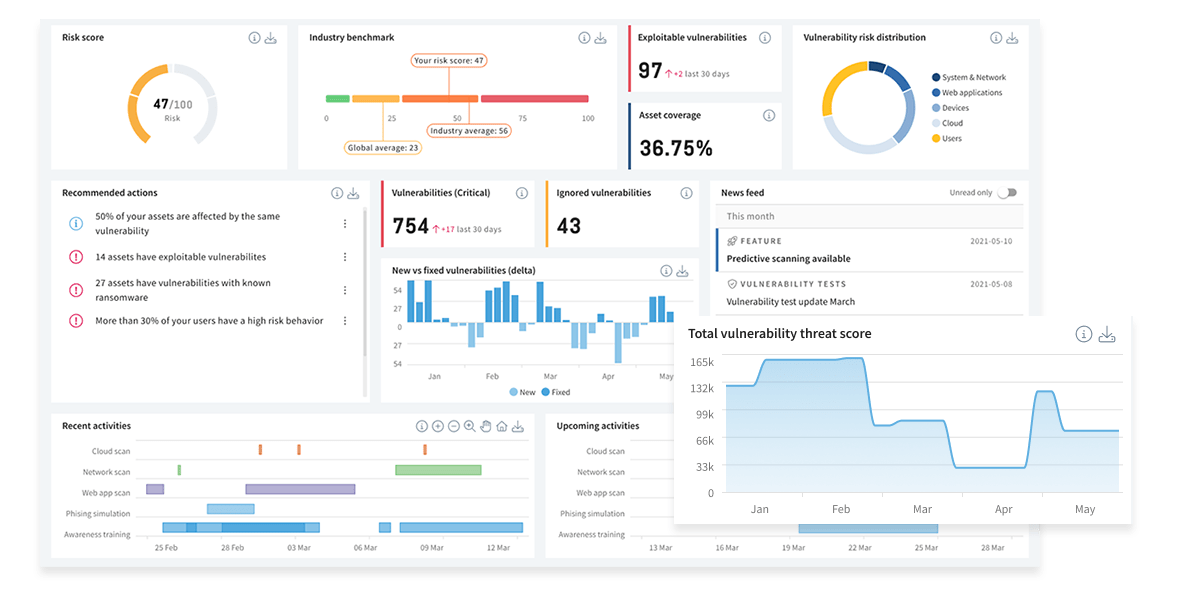
Identify vulnerabilities across your entire attack surface, covering both your technical and human assets with Holmsecurity. All in one unified platform. One risk model. One workflow.
Unparalleled Attack Vector Coverage
cybersecurity companies in uae
Our Next-Gen Vulnerability platform continuously detect vulnerabilities and protect your organization against cyber security attacks such as phishing and ransomware. Get unparalleled attack vector coverage with Holmsecurity vulnerability management platform.
Secure the Modern Attack Surface
Keep up with current threats and protect your entire infrastructure, including cloud, operational technology, and remote workforce. Our all-in-one platform offers unparalleled insight and visibility, covering all your assets across your organization’s technical assets, including local and public systems, computers, cloud infrastructure and services, networks, web applications, APIs, and human assets - your users.
A Truly Unified Platform - No More Silos
Our platform represents, or replaces, up to six different products (systems, computers, cloud, web, APIs, IoT, OT/SCADA, etc.). We provide a truly unified view with unified risk scoring. This allows you to understand the full context of each exposure and focus on high-risk technical vulnerabilities and users. Maximize your efforts and reduce business-critical risks with the least amount of effort
Cloud Scanning
Manage your cloud infrastructure, including Infrastructure as a Service (IaaS), Software as a Service (SaaS), and Platform as a Service (PaaS), in one unified view. Gain complete visibility and actionable context on your most critical misconfigurations related to network access, encryption, user permissions, access control, least privilege. By doing this, your teams can proactively and continuously improve your cloud security posture. Enjoy the core capabilities of CSPM and vulnerability management in the same platform.
Take Control of Cloud Misconfigurations
Gain complete visibility and actionable context on your most critical misconfigurations, so your teams can proactively and continuously improve your cloud security posture.
Detect & Respond to Threats Faster
Empower security, development, and operational teams to efficiently prioritize and remediate risks in cloud native environments as early as possible in the application development life cycle.
Multi-Cloud Visibility & Asset Management
Manage your full asset inventory across all your cloud platforms services, resources, regions, accounts, and divisions.
Cloud Identity & Access Management
Reduce risk to your organization by maintaining least-privilege access for cloud workloads, data, and applications.
Cloud Scanning Featured Capabilities:
Discover and Visibility
Easily Manage Your Cloud Environment in One Unified View. Cloud Scanning provides visibility into your cloud services and resources and their security configurations. This gives you a single source of information across your cloud platforms. Cloud assets, as well as resources used, are automatically discovered during the automated discovery scans and then scanned for misconfigurations.
Misconfiguration Management
Automatically Identify Misconfigurations. Cloud Scanning minimizes your cyber security risks and accelerates the remediation process by comparing cloud application configurations to compliance policies to identify gaps quickly. The recommended remediations could include fixing misconfigurations related to network access, encryption, user permissions, access control, and least-privilege.
Proactive Threat Detection
Strengthen Your Security Defenses. With Cloud Scanning, alerts are reduced by presenting you with areas most likely to be exploited through risk scoring. Vulnerabilities can then be prioritized, so misconfigurations are ultimately prevented from becoming a security risk.
System & Network Scanning
Safeguard your organization from costly security breaches. Detect vulnerabilities, assess risk, find blank spots, and prioritize remediation efforts for all assets across your organization. Scan your public and local systems, local and remote computers and devices, cloud infrastructure, network devices, and IoT, with additional coverage in Operational Technology (OT) and SCADA environments. Address individual threats, exploits, and regulatory non-compliance.
Security Measures
Enjoy a high level of security without any complexity. Run scans effortlessly on networks or servers looking for over 100,000 vulnerabilities.
Scan Full Attack Surface
Scan for vulnerabilities in outdated operating systems, services, and software. Check for misconfigurations, including insufficient permissions and exposed data.
Be Notified
Get notifications when new vulnerabilities are found, or unusual changes occur in the network, such as exposed ports or services.
Extend Asset Coverage
Scan your portable devices, including laptops, wherever they are with our lightweight endpoint Device Agent.
System & Network Scan Featured Capabilities:
Response with Faster Detection
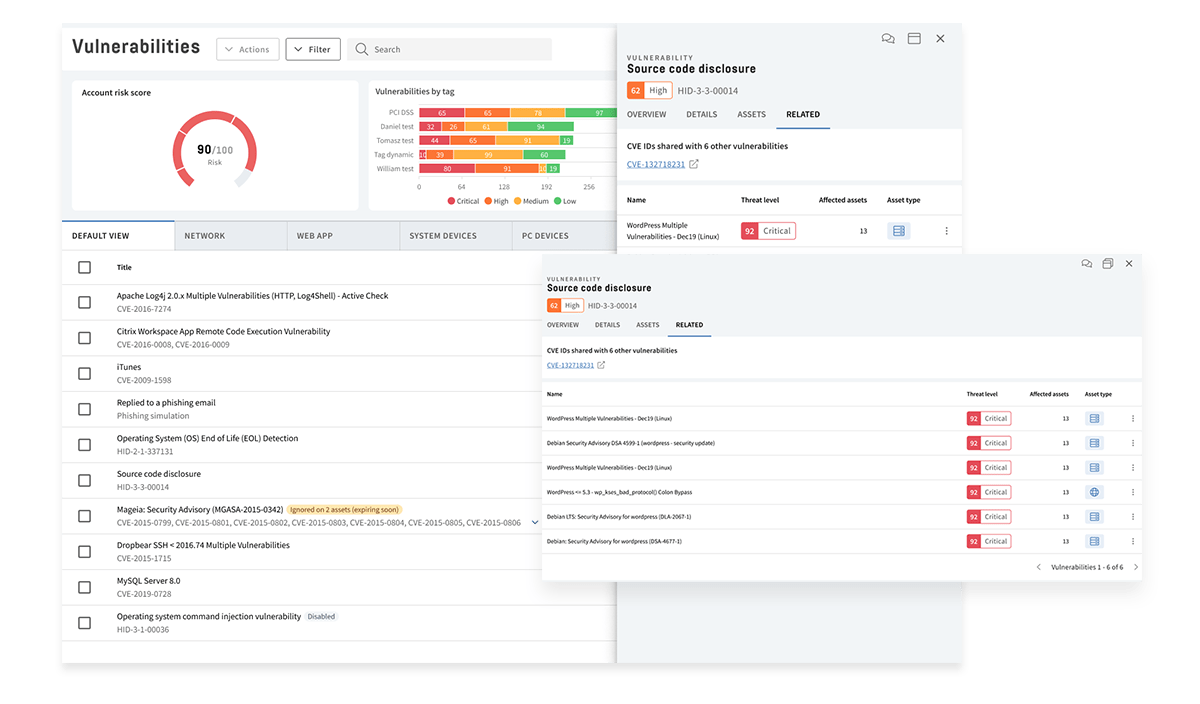
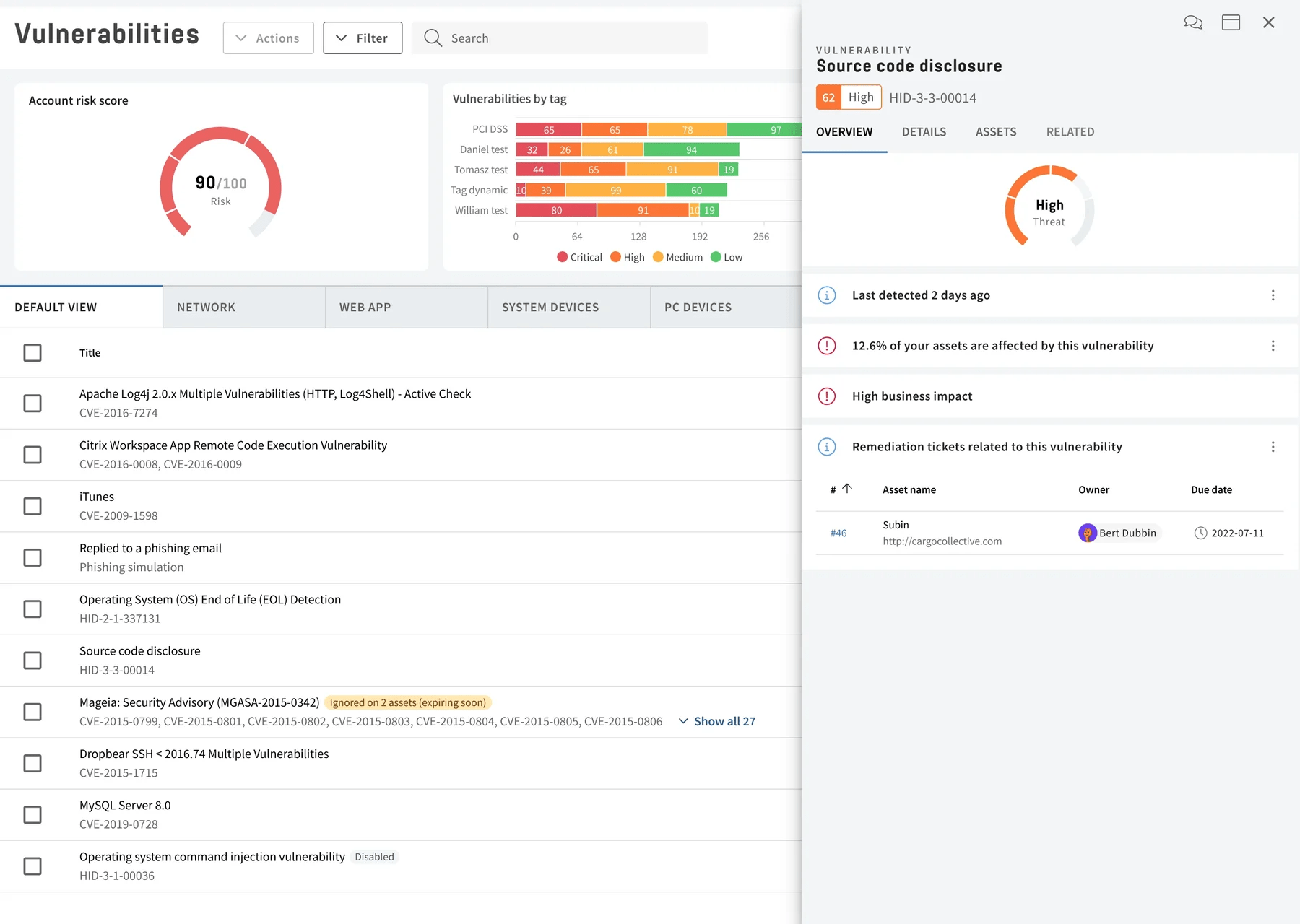
Manage all vulnerabilities with the market's most flexible and powerful vulnerability management workflows. Sort, group, and prioritize vulnerabilities.
Optimize the Remediation Process
A complete workflow for remediation, supporting integrations with external systems such as Jira and Top Desk.
Respond Quickly & Eliminate Delays
Get instant notifications by email, SMS, Slack, or Teams, when new vulnerabilities are found or when there are changes in your network with rule-based monitoring.
Amplify Your Security Efforts with Integrations
Make vulnerability management a part of your work process and routine. We provide out-of-the-box integrations with a wide range of systems like SIEM, CMDB, patch management, ticketing systems, and CI/CD
Meet Today's & Future Compliance
Along with the growing threat picture, there are new legal requirements, directives, standards, recommendations, and certifications that are continuously introduced. We help you meet existing and future requirements such as NIS, NIS 2, GDPR, ISO27001, and PCI DSS.
Web Application Scanning
Stay on top of your web application security by continuously detecting thousands of vulnerabilities with our Web Application Scanning product. Understand your current threat landscape and adopt a proactive approach to information security. Detect vulnerabilities related to harmful code, misconfigured systems, weak passwords, exposed system information, and personal data.
Market leading scanning capabilties
Our web application scan engine supports multiple technologies, such as modern web apps built with JavaScript and multiple authentication methods, including recording of login sequences using our web recorder.
Covers a broad range of vulnerabilities
Discover unknown vulnerabilities within cross-site scripting (XSS), SQL injection, insecure file uploads, insecure storage of sensitive data, authentication, input sanitization, SSL, encryption misconfigurations, and much more.
Effective Remediation
Do not get lost in all the data. Understand what vulnerabilities to remediate first with automated assessment for prioritization.
Automatic & Continuous
Automatically discover new assets that are connected to the network. New vulnerabilities are quickly identified through scheduled and continuous scanning.
Web Application Vulnerability Scanning Capabilities:
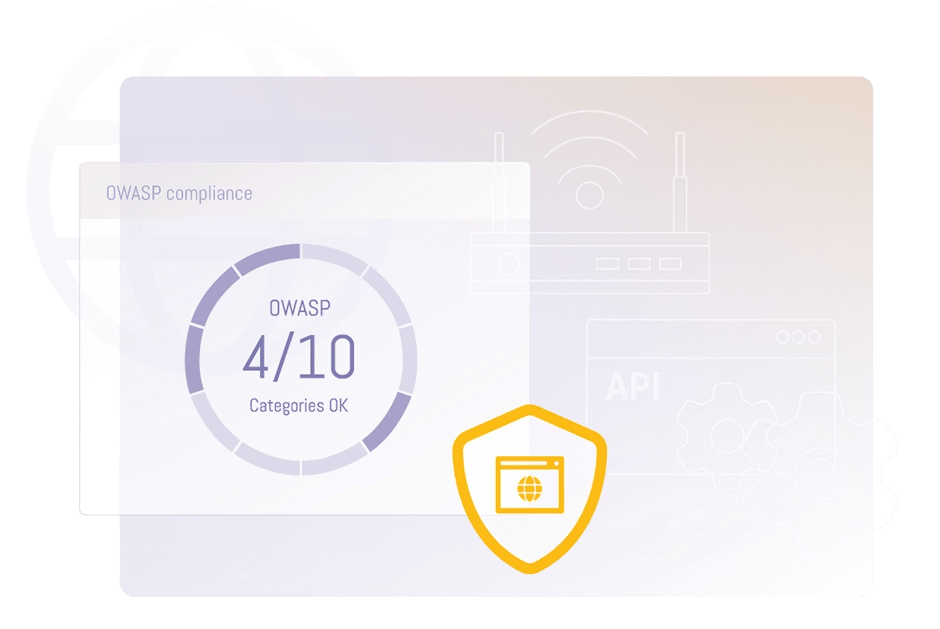
OWASP Top 10 & Much More
Our web application scanner finds a wide range of vulnerabilities, among others the OWASP Top 10. OWASP Top 10 is a widely recognized list of the top 10 most critical web application security risks compiled by the Open Web Application Security Project (OWASP). OWASP Top 10 covers vulnerabilities like injection, Cross-site scripting (XSS), and security misconfiguration.
Phishing and Awareness training
Build your human firewall by having your employees recognize cyber threats and phishing attempts in a safe and controlled environment with phishing simulations and automated and tailored awareness training. Take steps towards increasing cyber security awareness, protecting sensitive and personal information, and avoiding costly data breaches and ransomware.
Out-of-the-Box
Cover a wide range of phishing scam simulations and scenarios, including ransomware, spear phishing, CEO fraud, and more
Awareness Training
Our platform supports the entire workflow, from simulation to awareness training and questionnaires. Get started with ready-made templates or customize them to suit your organization. misconfigurations, and much more.
Nano Learning
Educate employees with tailored best-in-class awareness videos and cyber security training. Provide content based on simulation behavior.
Measure Risk & Trends
Get behavioral reports per department, recipient, or location. Identify weak spots and strengthen your human defense. Track individual risk scores over time.
Phishing & Awareness Training Capabilities:
Ready-Made Phishing Templates
Choose from our extensive template library that includes ready-to-use templates for simulations based on classic and current scenarios.
Out-of-the-Box Awareness Training
Out-of-the-box multi-language templates for awareness training and questionnaires.
Best-in-Class Videos
Video content for awareness training based on short and modern videos in your local language.
Nano Learning Concept
The awareness training programs are based on nano learning, where training is focused on small, bite-sized pieces of information. This makes it easier to absorb and retain information.
API Scanning
Elevate your API security effortlessly with our game-changing solution. Leave no potential entry points unscanned or exposed to attacks. Our advanced scanning technology ensures complete visibility and resolves vulnerabilities, safeguarding your externally facing applications with confidence. Experience the future of API security today.
Transform Threats into Priorities
Our platform finds and categorizes your high-risk vulnerabilities automatically, converting them from potential threats into top priorities for your team.
Your Schedule Your Scans
Set your own schedule for continuous scans and let the platform handle the rest, giving you more time for strategic planning.
Scans for OWASP Top 10 API Vulnerabilities
Find vulnerabilities with tailored security scans, such as security misconfigurations and injection flaws, from the OWASP Top 10 API security list.
Cover Multiple Attack Vectors Simultaneously
Identify gaps in your cyber security defense across your entire attack surface. View your vulnerabilities from the organizational level right down to a singular API.
API Scanning Featured Capabilities:
Your Shield Against API Threats
Effortlessly fortify the security of your APIs, guaranteeing equally robust protection as offered to web applications and websites. With Holm Security, you can:
- Conduct thorough scans of your REST, GraphQL, and SOAP endpoints to identify and resolve any security flaws. Quickly assess the security of your APIs
- Keep entry points for attacks secure and ensure your APIs are always up-to-date.
- Attacks can happen at any time. But that doesn’t mean you have to live in fear. Automate scans – so you can be confident you’ll catch new vulnerabilities quickly.
Complete Coverage Through Detailed Scanning
- Get complete visibility of your API endpoints, including coverage for REST APIs, SOAP APIs and GraphQL API
- Find vulnerabilities with tailored security scans, such as security misconfigurations and injection flaws, from the OWASP Top 10 API security list.
- Perform scans that provide a 360-degree view of your API security, inside and out. Never miss a beat with our all-encompassing scans.
Incorporate into Your Tech Stack for Effortless Collaboration
- Work in Harmony with Your Team. Effortlessly integrate with your tech stack, including popular platforms like Slack, Jira, Github, and more. Because teamwork really does make the dream work.
- Showcase Your Security Prowess with Detailed Reports. Impress your stakeholders and/or customers with comprehensive reports demonstrating your commitment to security; Because seeing truly is believing.
INTEGRATION
Out-of-the-Box Integrations
SIEM
Act in real-time with up-to-date situational awareness and comprehensive security analytics. Integrate with your SIEM systems like Microsoft Sentinel, IBM QRadar, LogPoint, and Splunk.
TICKETING & CMDB
Integrates to automatically open tickets for vulnerabilities and close them when they have been resolved. Integrate with Jira, TopDesk, and more.
NOTIFICATION
Link vulnerabilities with the asset’s business criticality, and prioritize issues based on this data to accelerate remediation. Integrate with ServiceNow and other services.
CI & CD
Integrate with tools for Continuous Integration and Continuous Delivery (CI/CD) to help automated processes. Integrate with Jenkins and other services.
COMPLIANCE
Meet Today's & Future Compliance
NIS & NIS2
The NIS and NIS2 directive (decided December 2022, and comes into effect 2024) requires a systematic and risk-based cyber security approach. Holm Security helped hundreds of organizations to be compliant with the NIS directive.
GDPR
Our platform help organizations meet GDPR (General Data Protection Regulation) requirement for regular security assessments and vulnerability testing to identify and address potential vulnerabilities.
ISO27001
To be compliant with ISO27001, an organization must establish and maintain an Information Security Management System (ISMS) that meets the requirements of the standard. This includes conducting risk assessments.
PCI DSS
We provide PCI DSS compliance scanning for payment card processing environments that meets the security standards set by the PCI DSS. Our platform is listed as a ASV scan solution (Approved Scanning Vendor) in cooperation with our partner Akati.
Product Demo
See HolmSecurity Next-Gen Vulnerability Management Platform in action.
Schedule a demo now with Bulwark Technologies and experience the full capabilities of Holmsecurity Next-Gen Vulnerability Management Platform.
Schedule a FREE Demo
"*" indicates required fields
