Cybersecurity Solutions
Digital Risk Monitoring
cybersecurity distributor in UAE
With Risk™ from Resecurity, receive actionable risk intelligence about any significant changes to your security posture
01
In-depth risk evaluation of the entire enterprise.
02
Early-warning security notifications.
03
Automated daily security posture reports.
04
Data is displayed on a convenient dashboard.
Risk™
Digital Risk Monitoring
Time is our most valuable resource in cybersecurity. Leverage RiskTM to automate your digital risk management and receive insight about any significant changes to your security posture due to Dark Web, data breach, compromised credentials, network infections and other security incidents.
Capabilities Of Digital Threat Monitoring

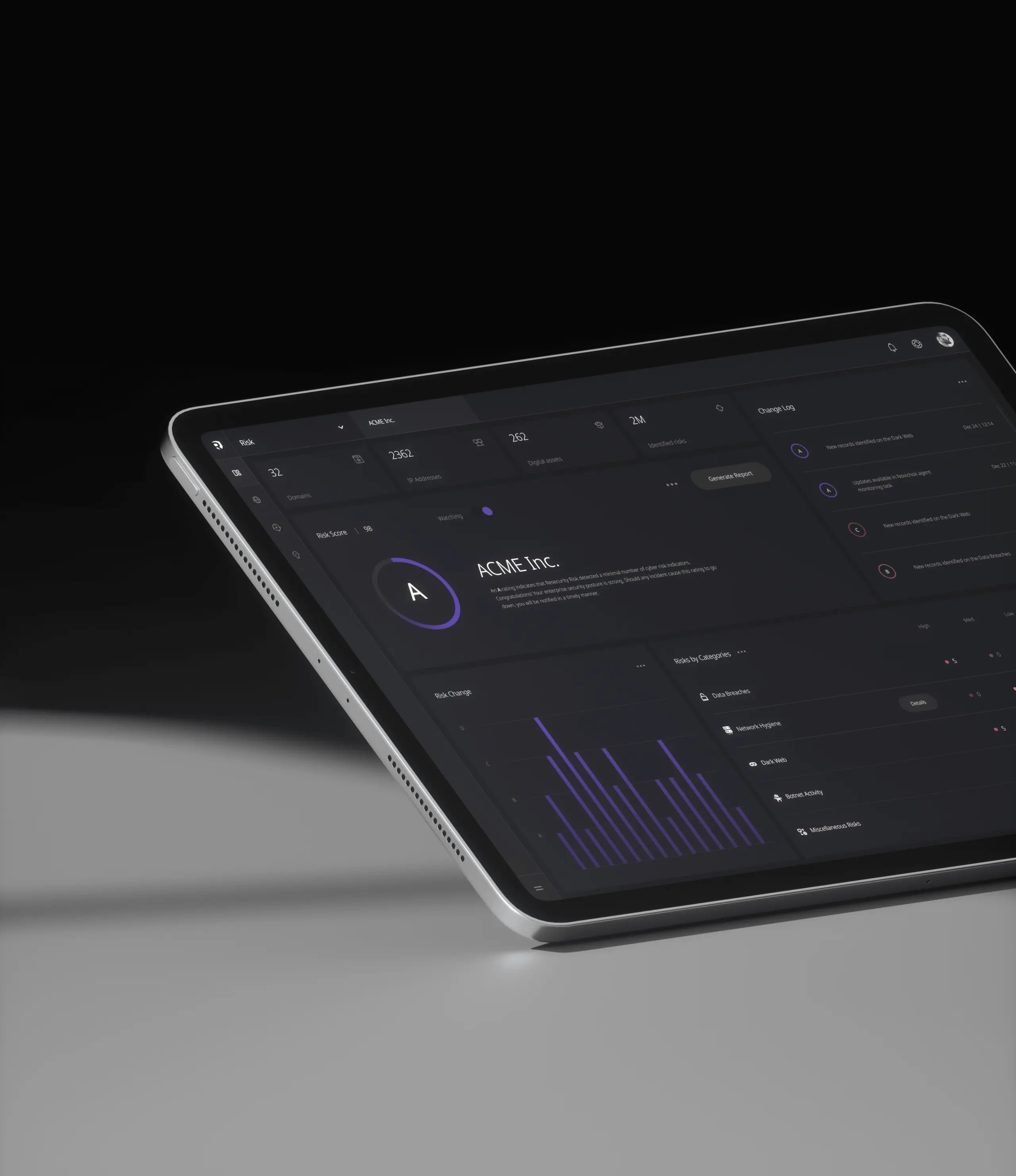
Measure Risk
Your daily security score is rated based upon a summary of all risks for your monitored domains, IPs, networks, vulnerabilities, and cloud services. Actionable intelligence with immediate remediation is key to achieving a high security score.
- Unparalleled risk management
- Actionable intelligence that makes a difference
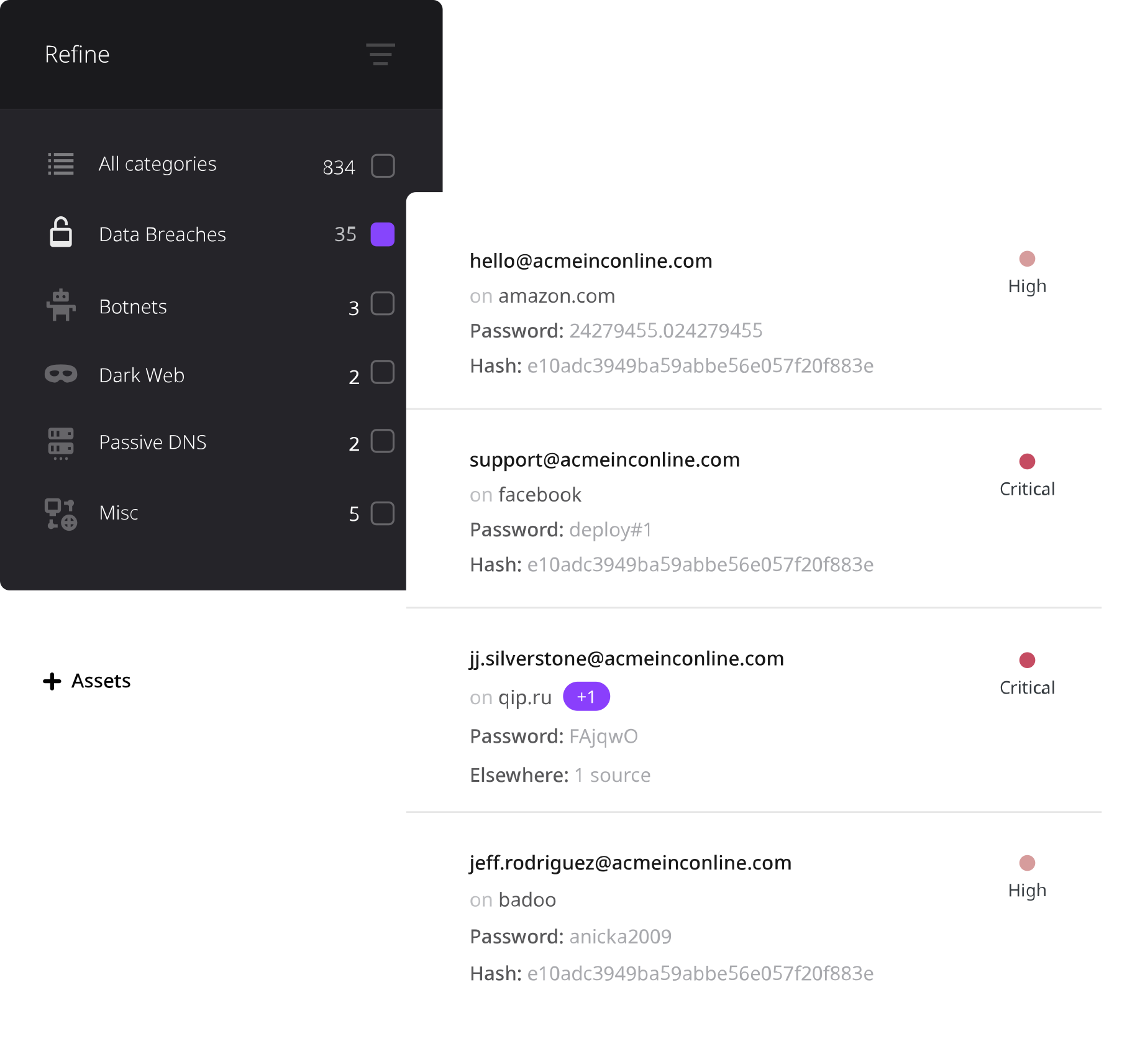
Risk Assessment
Refine and enrich datapoints to understand where weaknesses and vulnerabilities in your digital assets are. Changes and updates are sent through notifications via reports or e-mail as new data is discovered.
Risk Categories
Identify external threats based upon high-quality intelligence aggregated from over 20,000 public and closed sources
External
Risk Vectors
- Account Takeover
- Botnet infections
- Business E-mail Compromise
- Cyberspionage
- Brand Reputation Abuse
- Dark Web Activity
- Domain Squatting
- Data Breaches
- Digital Certificates
- Exposed Network Services
Internal
Risk Vectors
- Active Directory Account Compromises
- Backdoors
- Incorrect Network Segmentation
- Security Anomalies
- Lateral Movement
- Malicious Traffic
- Vulnerable Software
- Misconfiguration Errors
- Unpatched Services
Cloud
Risk Vectors
- Abandoned EC2 instances
- Exposed Databases
- Compromised Credentials
- Sensitive Data Identification
- Misconfigured services
- Malicious code
- Public S3 bucket with sensitive data
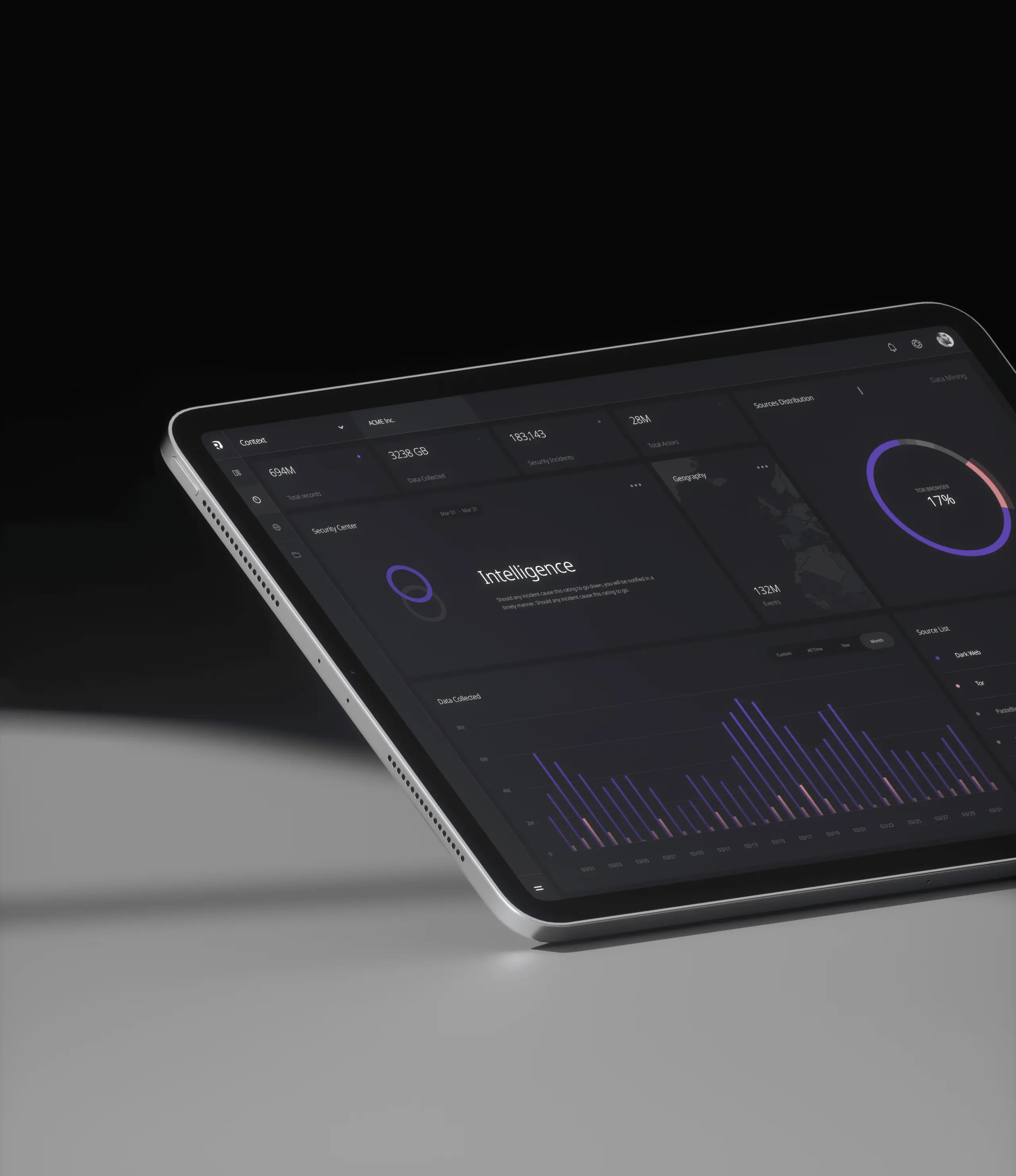
Global Visibility
Our geo-location capability delivers contextual information identifying low, medium and high-risk areas for managing your infrastructure, network resources and other company assets.

Download Datasheet
Comprehensive Digital Risk Monitoring Powered by Risk™
Resecurity provides proactive alerts and comprehensive visibility of internal and external risks targeting the enterprise. Reduce potential blind spots and security gaps with Risk™.
Product Demo
Try Resecurity Digital Risk Monitoring - Risk™
Schedule a demo now with Bulwark Technologies and experience the full capabilities of Resecurity™ Digital Risk Monitoring Solution powered by Risk™
Schedule a FREE Demo
"*" indicates required fields
